There is very often a fallacy in the world of Cybersecurity that simply implementing various types and kinds of Security Technologies towards the lines of defenses of a business or a corporation will mean greater levels of protection. While in theory this may be true, but reality often dictates the opposite of this. For example, by simply deploying various Security tools, you are actually increasing the attack surface for the Cyber attacker. For example, a CIO or a CISO may think that deploying ten firewalls is better than just having one in place. But with this thinking, they have given the Cyberattacker nine more avenues in which to attack the vulnerabilities and weaknesses of the IT Infrastructure.
Instead, it is far better to spend the critical financial resources for perhaps just two firewalls, but making sure that they are strategically placed they are needed the most and will have the most effect. This kind of mindset of determining where Security Assets need to be placed is actually a very proactive one. The primary reason for this is that the CIO/CSIO and their IT Security staff are actually taking the time to discover what areas are most at risk in their organization, what tools will be most effective and where, rather than spending money in a haphazard fashion. In fact, this proactive way of thinking needs to be extended to the world of Threat Hunting as well.
With this, the IT Security staff are using various kinds of methodologies and tools in order to scope out and mitigate the risks of any Cyberthreats that are lurking from within their IT Infrastructure. But being successful at doing this on a daily basis requires that the CIO/CISO and their IT Security staff have to go above and beyond the proverbial “extra mile”.
How this can be achieved is reviewed in this article.
A Formal Definition of Proactive Threat Hunting
A formal definition of proactive based Threat Hunting is as follows:
“[It] is the process of proactively searching through networks or datasets to detect and respond to advanced cyberthreats that evade traditional rule- or signature-based security controls. Threat hunting combines the use of threat intelligence, analytics, and automated security tools with human intelligence, experience and skills.”
(SOURCE: 1)
In other words, there are two sub components of this definition:
Being proactive in any type of Threat Hunting exercise means that the CIO/CISO has to break away from the conventional ways of thinking, and have the ability to “think out of the box”. For instance, what works in one situation more than likely will not work in another, because the Cyberthreat landscape is changing on a very dynamic basis.
Being proactive simply doesn’t involve the use of the latest and most sophisticated of Threat Hunting tools. Rather, it takes not only that, but also the use of reliable information and data as well as deep motivational levels, experience, and technical know-how from the IT Security staff.
This is illustrated in the diagram below:
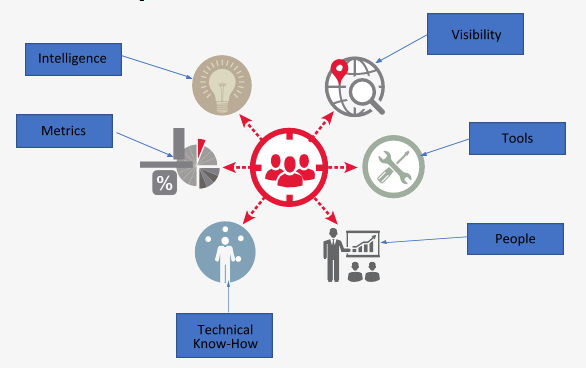
(SOURCE: 1)
Despite the importance of Threat Hunting in Cybersecurity today, not too many businesses and corporations are implementing it, which is pointed by these stats in a recent survey in which 306 organizations were polled:
Only 27% of the respondents actually had a well-defined Threat Hunting methodology and were actually utilizing it;
Only 45% of the respondents had a formal plan in place in order to launch and execute a specific Threat Hunting exercise.
(SOURCE: 2)
Other stats:
88% of businesses feel that their existing Threat Hunting approaches need to be greatly improved;
56% of organizations feel that conducting a Threat Hunting exercise with their own resources (or “in-house”) takes too long and consumes resources from carrying out other IT Security related duties;
53% of organizations feel that their Threat Hunting methodologies and activities are actually “tipping off” Cyberattackers.
(SOURCE: 3)
Why are businesses and corporations not taking a proactive approach to Threat Hunting? The following reasons are cited:
The use of different tools can make Threat Hunting a very time-consuming proposition;
The collection of information and data can be a very labor-intensive process which requires third part involvement and verification;
There is not enough time to conduct proactive based Threat Hunting exercises because the IT Security staff has to respond to so many false alarms that are sounded off on a daily basis;
Because of the enormous time constraints that are involved, only about 1% of all Security Alerts are actually probed into and further examined
(SOURCE: 4);
Threat Hunting can be a huge financial drain;
Threat Hunting requires a very special kind of mindset – recruiting candidates for this specific talent can be very difficult.
Despite these above-mentioned obstacles, proactive Threat Hunting is still a much-needed function for every business and corporation and is a process that can be achieved.
Conclusions
In our next blog, we examine how your IT Security staff can actually initiate the Threat Hunting process and the various components that are involved with it.
Sources
https://www.raytheon.com/sites/default/files/cyber/rtnwcm/groups/iis/documents/content/proactive-hunting-datasheet.pdf
https://www.darkreading.com/partner-perspectives/juniper/proactive-threat-hunting-taking-the-fight-to-the-enemy-/a/d-id/1331084
https://go.crowdstrike.com/rs/281-OBQ-266/images/WhitepaperProactiveHunting.pdf


