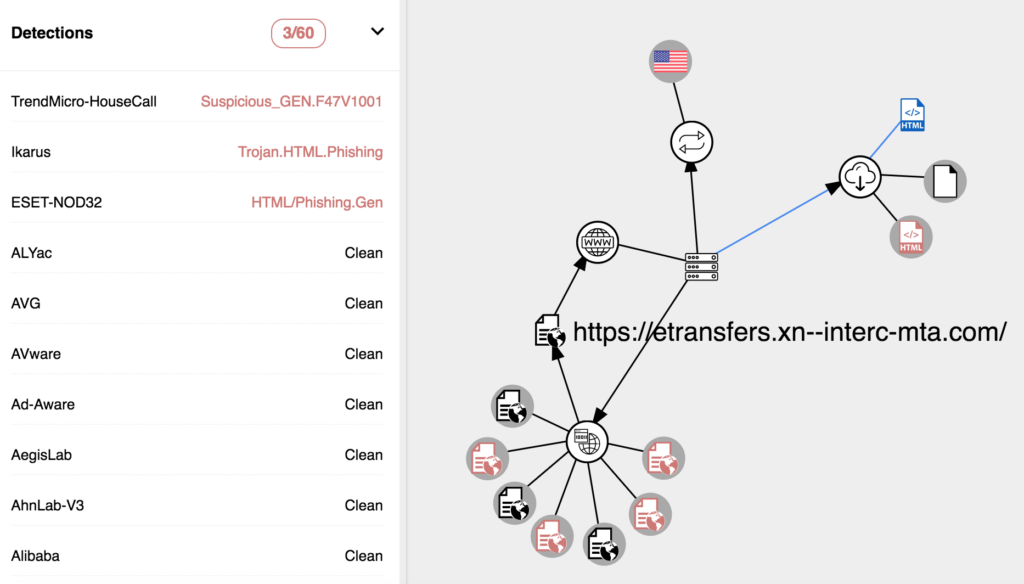
I received a mysterious text message the other day, apparently from the Canada Revenue Agency (CRA) telling me to “complete your form, and give us 10 working days to process your claim”. Of course, I always like to observe cyber attack attempts like this first hand to see how complex (or not) the phishing is getting. This one was interesting and is a good lesson on how to spot a phish.
I received a mysterious text message the other day, apparently from the Canada Revenue Agency (CRA) telling me to “complete your form, and give us 10 working days to process your claim”. Of course, I always like to observe cyber attack attempts like this first hand to see how complex (or not) the phishing is getting. This one was interesting and is a good lesson on how to spot a phish.
First, there was the message itself, and the exposed URL:
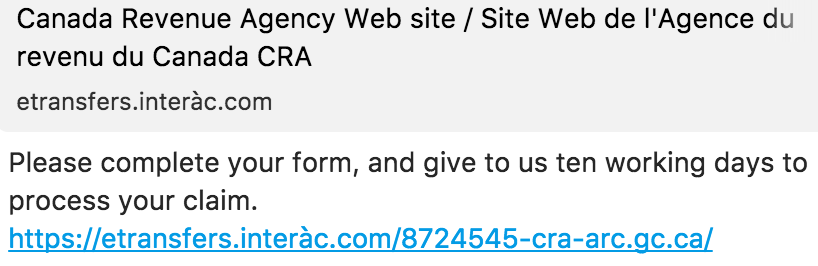
Other than the fact that CRA doesn’t text message you (that I know of), there were some other signs.
First, the phishing link had a French accent in it, which was unusual in a couple of ways. When a web browser is faced with an accented character (Unicode) in the hostname like café.com, it needs to decode it from Unicode (which is the visually correct looking word) to Punycode (an ASCII representation containing only Letters, Digits and Hyphens – LDH) in order to allow a DNS server to understand it. Domain Name System services only use ASCII in their records. (NOTE: IDNA – Internationalizing Domain Names in Applications encoding exists so web browsers can translate any international domain name (for example, one with accents or double-byte characters) into a recognizable ASCII domain. These domains are first translated to Punycode and then have a prefix of “xn--” appended to the front of the record. As an example, the Russian top-level domain extension is “рф” which is “xn--p1ai” in IDNA).
So the URL in the text message,
![]()
gets translated from the semi-legitimate looking URL you see, to the following below:
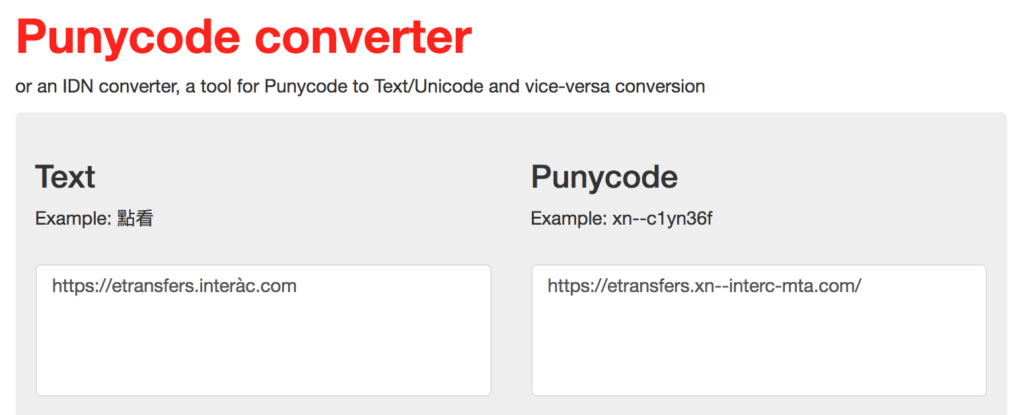
Obviously, if you saw the DECODED domain in ASCII Punycode (shown on the right in the above image), it would look strange and you likely wouldn’t click it. But an accented letter in a URL is actually a good way for an attacker to get a phishing domain that looks reasonably legit. (EDITORS NOTE: the Unicode character U+0430 is a small Cyrillic “a” and would have been a better choice than the accented “a”). Anyhow, the accent in the string “interac” raised flag #1.
So, the domain that is shown on the left (with the accent) doesn’t actually exist “as-is” because as I mentioned, the Domain Name System does not allow for non-ASCII records. The domain on the right does exist, however (even though the site has since been suspended). A little bit of research into the “real” Punycode domain shows that it is hosted at Namecheap Inc. This is a discount hosting provider where you can get a hosted server for about $1 per month….another telltale sign of phishing or malware….hackers can be very cheap!
Finally, the most important item that people need to be aware of is WHERE to look in the URL to determine if it is a phish. In the example of the Punycode URL sent to me, there is a string in the text message that had “cra-arc.gc.ca” in the URL. This is actually the real domain for the Canada Revenue Agency. So where to look??
Some Examples:
In the example httx://abc-555.xyz.def.com/1234-mno.pqr.com, you need to focus on “DEF.COM”. This is the top-level domain of the web server…and you are ultimately going to a location that is theoretically owned by the owners of “DEF.COM”.
In another example, httx://abc.123.mnop.com, the top-level domain is “MNOP.COM”.
The rule of thumb for how to identify the top-level domain is:
- look at the first two fields, separated with a dot, that are located to the left of the first single forward slash, OR
- look at the first two fields, separated with a dot, that are at the end of the URL (if there is no single forward slash.
When you have these items, assess if this looks like a real domain. Of course, this doesn’t completely protect you. Mainly because the real domain may have been compromised and the owners don’t know it yet, or you just don’t know if the domain is real or not. When in doubt, always choose NOT to click the link!!
One final point…email phishing attacks are still, by far, the number one method of successful cyber attack because they work. If you are interested in learning how to properly defend against phishing attacks for your company, contact us at evolve@cyberhunter.solutions. We can help you eliminate the number one method of successful cyber attack in less than the time you spent reading this blog post.