Even though it has been over two decades since the first phishing attack (we all remember the Nigerian scams that asked users for their bank details and offered a share in a fortune in return), phishing attacks still remain one of the top threats to organizations. The only difference now is that cybercriminals have evolved from less sophisticated impersonations to adopting modern collaboration and communication tools. “Phishing Is No Longer Just Email: It’s Social.”
Giants like Qatar Airways, Target, and PayPal have made headlines over the years for falling victim to phishing attacks where cybercriminals impersonated their companies and targeted consumers. In a recent phishing scheme and Trojan malware, cybercriminals tricked Netflix users into providing bank credentials and passwords to sell the information on the Deep Web.
According to a report by the FBI’s Internet Crime Complaint Center, people have lost nearly $57 million as a result of phishing schemes in one year!
In this blog post, we discuss how businesses can better identify phishing attacks to avoid falling victim to them and ramp up their cyber security efforts for further prevention. We will also highlight how a professional cyber security service can reduce security lapses by conducting cyber threat hunting and network security audits.
Spot The Signs Of A Phishing Attack
Email impersonation is the core of most phishing attacks. The attacker uses legitimate email addresses (with spoofed domains) to look like they’re from a brand you trust – like a social networking site, a credit card company, a bank, or an online store.
Let’s look at a phishing scenario where the cybercriminal impersonates FedEx. The easiest route that the attacker could take is through a domain variation that resembles the authentic email address. So in this case, if the real identity is: contact@fedex.com, the attacker could use the following variants to create convincing top-level, sub, or root domains:
- contact@fedex.men
- contact@fedexs.com
- contact@fedex_outbound.com
Notice the minor—usually overlooked—differences in the spoofed domains?
Additionally, the attacker can simply change the display name to the organization. As a result, the spoofed domain will use the FedEx Customer Service display name to bait the users.
Here’s a real-world example of the Netflix phishing email:
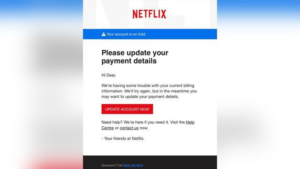
At a glance, this email might look real, but it’s a scam. Here are some subtle signs:
- An international business like Netflix probably wouldn’t use a generic greeting “Hi Dear”
- A telltale sign of a phishing email is that there’s usually a malicious link at the end that requests for payment information.
There’s a dedicated help page on the Netflix website that advises subscribers on how they can identify and handle suspicious emails that look like they’ve come from Netflix.
Protecting Yourself from Phishing Attacks
While phishing can’t be entirely avoided, there are some ways SMBs can prevent these attacks:
- Educate employees and conduct training sessions with mock phishing scenarios
- Keep systems current with the latest security updates and patches
- Deploy a SPAM filter to detect blank senders and viruses
- Isolate critical parts of your company’s infrastructure and encrypt all sensitive information
- Implement a centralized network security solution
While you can’t stop your employees from unintentionally clicking on malicious links, it’s always a good idea to implement a central firewall to filter out potential cyber threats. At CyberHunter, we offer advanced cyber threat hunting, penetration testing, and network security audit services that can help minimize the harm to your business.
Get in touch with us to book a discovery meeting or request a quote for our services today.


