Let us find the weak links in your financial services network and web applications.
Cyber Security & Penetration Testing for Financial Services Institutions
We provide banks and financial services with state of the art cyber security consulting services and leading edge penetration testing services. We provide network vulnerability mapping, exploitation attempts, social engineering, and real-time cyber threat analysis for banks and financial services organizations in North America and the Caribbean.
What is included in Cyber Security Penetration Testing for a bank or financial services organization?
Vulnerability assessments and penetration testing are terms that are used interchangeably but are ultimately different services.
In plain terms, if we imagine that your application or network is a locked door, a vulnerability assessment trying to identify all the possible locks that exist on the door. Penetration testing, on the other hand, is where an ethical hacker takes their big bag of “keys” (these are tools, techniques, and procedures) and attempts to open each one of the locks with every single “key”, hoping to open the door — but with permission.

What Type of Pen Test Does Your Financial Institution Need?
In general, there are two categories of penetration testing or “pen test” that banks or financial services institutions usually require: customer-driven / compliance-driven, OR penetration tests that attempt to exploit people, process or technology with the objective of breaking into the network and gaining access to digital assets.
Scenario 1 Penetration Test
Customer-Driven or Compliance-Driven
Example: “We have a web application and one of our biggest clients need us to get a 3rd party pen test performed for their risk team”.
This scenario actually describes a vulnerability assessment, followed by a blend of automated and manual pen testing that looks for obvious configuration flaws or vulnerabilities that can be exploited without too much effort. The main goal is to produce a remediation report on the issues that let you harden your website, application or network. This can also be considered a security audit of sorts, particularly when a specific set of metrics are used for compliance measurement (e.g. PCI-DSS compliance) or if we are looking at analyzing the running configuration of a device. CyberHunter will produce a comprehensive Penetration Test Report detailing the exact method of testing, Proof of Concept code for breach replication, all evidence and results of the testing, as well as remediation advice so you can fix your issues quickly and accurately.
Scenario 2 Penetration Test
Breach the Network (Red Team Exercise)
Example: “We are looking to test and improve our overall cybersecurity posture and we need an ethical hacker to try to break into our network.”
This scenario describes a more traditional penetration test. This type of pen test (also called a Red Team exercise) simulates an adversarial role and is a far more realistic way to test the security readiness of an organization. This testing covers exploitation attempts against People, Process, and Technology. It can involve a significant amount of social engineering and usually triggers active security controls and countermeasures inside the operating environment. These tests will additionally assess internal Blue Team (the defensive team) responsiveness and/or process in the event of an intrusion detection.
The right Cyber Security initiatives such as regular penetration testing can save your bank or financial services company from being the next headline.

PENETRATION TESTING FOR BANKS OR FINANCIAL SERVICE INSTITUTIONS
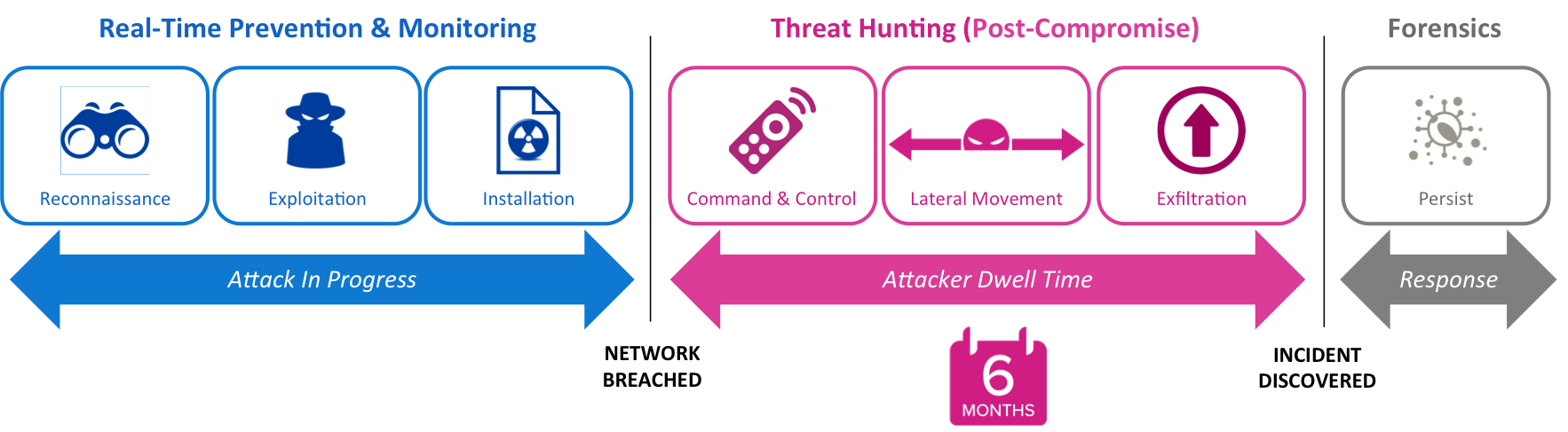
The initial phase of a penetration test is to take all the reconnaissance data, enumerated system data and every one of the identified theoretical vulnerabilities and attempt to exploit them the same way a hacker would. This is the Penetration Test or Pen Test and it is where all those theoretical weaknesses get exercised to see if there is way into the network or web application. Each pen test is customized to meet the needs of the client. Whether white-box or black-box, internal or external, wireless or wired…we even perform social engineering tests to see if we can ethically hack into your organization.

More than Traditional Pen Testing
Normal penetration tests provided to financial services institutions live in a world that only looks at how to exploit KNOWN, theoretical vulnerabilities. These tests do not address zero-day flaws in security controls or applications. These tests are also limited by the skill of the ethical hacker doing the testing.
At CyberHunter, we provide a full suite of cyber security services including advanced penetration testing. Traditional pen testing for a bank as an example is only the starting point. We also hunt for breach and compromise that has ALREADY happened. Every single minute of the day your banking network perimeter, your bank employees and your financial web applications are being pen tested by thousands of adversaries.
CyberHunter Solutions Pen Test 2.0 has built-in threat hunting that works to identify Advanced Persistent Threats (APTs) and Zero-Day malware that has already breached the banking network. Get the world’s most advanced banking or financial cyber security services and penetration testing with CyberHunter.
Test Evidence and Reporting
The following flavors of testing and reporting are available from CyberHunter:
- Technical Detailed Report
- Executive Briefing
- Remediation Report
- MS Patch Reports
- PCI Compliance
- HIPAA
- SOX
- ISO 27001/2
- OWASP
- Center for Internet Security (CIS)
- US DoD STIG
- NIST CVE
- SANS Policy
CyberHunter can audit network devices as well: Cisco, Juniper, Palo Alto, HP ProCurve, Fortinet, Check Point, WatchGuard, Foundry and many others.
Four Key Cyber Security Principles for banks and financial services institutions
The following four key principles can help guide organizations in taking a more proactive stance in combating malware:
-
Accept that malware and APTs will breach existing defences.
-
Treat endpoints as untrusted until proven otherwise.
-
Trust established in an endpoint is both finite and fleeting.
-
Validate endpoints as malware free, anytime, anyplace.
Why Choose CyberHunter for your banking or financial services Cyber Security Consulting or Penetration Test ?
- The CyberHunter Pen Test 2.0 methodology leverages the most advanced tools, techniques and procedures in the industry to enumerate, identify and report on your existing security posture.
- We are the only threat assessment solution that can perform an advanced Vulnerability Scan and Pen Test while simultaneously hunting for, and identifying Advanced Persistent Threats that are ALREADY embedded in you network.
- CyberHunter gives you the insight and cyber intelligence you need for your bank or financial institution to be proactive.
BE PROACTIVE.
Trust in a network device is very temporary. Be proactive and ensure you scan, test and hunt on a regular basis.
TRUST NOTHING.
Security teams should NEVER trust an endpoint or server until it can be PROVEN to be trusted.
MALWARE CAN GET IN.
Companies need to prepare and be ready to respond to advanced persistent threats.