 In other words, they have invited the compromise onto their computer through their actions. Typically, the above situations represent over 95% of all successful attacks. Obviously a weak or poorly configured perimeter is another entrance method, but these are much easier to defend.
In other words, they have invited the compromise onto their computer through their actions. Typically, the above situations represent over 95% of all successful attacks. Obviously a weak or poorly configured perimeter is another entrance method, but these are much easier to defend.
A post-breach internal penetration test is all about the following:
You have assumed that you WILL be breached at some point and need to strengthen your security posture.
This type of testing is one of the most effective and realistic ways to measure the effectiveness of your overall operational cyber security posture (i.e. the People, Processes and Technologies protecting your environment). This will test your network visibility capabilities focussing on network traffic and endpoint behavior with a focus on the detection of potentially malicious operations. This testing can also be used to measure the detection and response capability of your security team or Managed Security Service Provider (MSSP).
A properly executed Post-Breach Internal Penetration Test is all about improving your operational cyber security posture. CyberHunter will deliver a comprehensive report that allows you to close the security gaps and maintain the Confidentiality, Integrity and Availability of your critical assets inside your environment.
Background of User-Driven Attacks
In order to combat today’s sophisticated cyber threat actor, complete situational awareness and network visibility is necessary. Traditional security infrastructure relies on the logging of security alerts to produce threat visibility. Unfortunately, security alerts and visibility are not the same. And without the ability to “see” the threats that are hiding in normal looking activities, you cannot possibly stop them.
Security alerts are created (and logged) when they detect something that they consider threatening. However, capable hackers do not do threatening things that ring the alarm bells. They rely on user-driven attacks and emulated “insider behavior” to do things that are silent, stealthy and VERY normal looking. In other words, they do not trip the alarm as they traverse the network, gaining access, establishing beachheads, and ultimately achieving their objective to steal, sabotage or damage corporate infrastructure and digital assets.
What is a “user-driven” attack?
Hackers have known for a long time that the easiest way to breach a network is not by attacking the perimeter, rather it is by socially engineering the users inside. If they are successful (and if they try hard enough they will be) a hacker will convince a user to do something that will lead to a compromise (e.g. open the malicious email, visit the bad website, plug in the unknown USB stick, or download the wrong application). All it takes is a small foothold, and a hacker will take over a user’s account and their machine. In other words, the hacker will become the insider. From there, everything they do looks like a user is doing it. If the hacker is good, these activities will look like normal behavior and will NOT be stopped, or even seen by traditional tools.
The CyberHunter Approach:
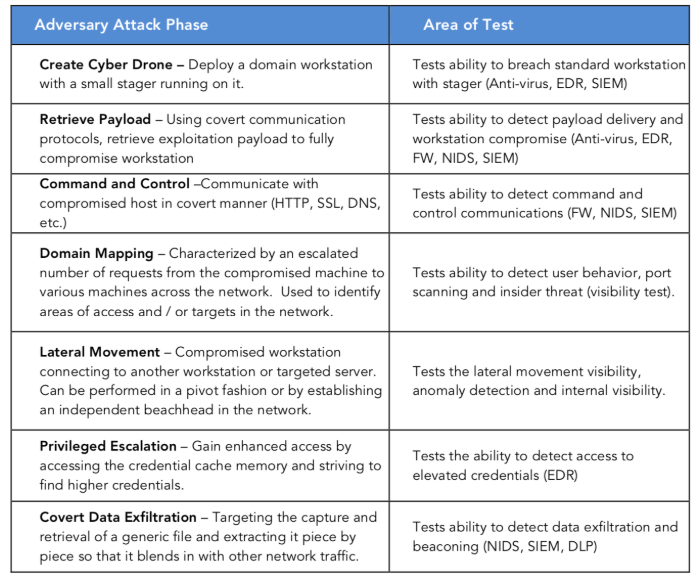
Internal Post-Breach Penetration Testing starts with the premise that an internal, trusted employee has “clicked the wrong link” or “opened the wrong email attachment” or “plugged in the wrong USB”. At this point, the adversary has a foothold inside the network and you have been actively compromised. This testing exercises the security controls, detection and response capabilities in the organization. For any internal assets being tested, CyberHunter shall employ a strategy that simulates a post-breach situation within the network (i.e. what can be done if an adversary has successfully breached the network perimeter).
To do this, CyberHunter will use its Cyber Drone software to establish a beachhead on a normal domain workstation, launching all activities from this location, using command & control techniques to communicate with the “compromised” system. Objectives for this testing are to evaluate the internal security controls, security visibility, detection capabilities, security team response to an adversarial threat, and to assess the overall security posture of the internal network. In some cases, specific objectives are set (e.g. retrieve a file from an elevated privilege file server). These can be discussed in more detail prior to the testing.


 In other words, they have invited the compromise onto their computer through their actions. Typically, the above situations represent over 95% of all successful attacks. Obviously a weak or poorly configured perimeter is another entrance method, but these are much easier to defend.
In other words, they have invited the compromise onto their computer through their actions. Typically, the above situations represent over 95% of all successful attacks. Obviously a weak or poorly configured perimeter is another entrance method, but these are much easier to defend.
