Discover the first truly all-in-one affordable cyber security solution purpose-built to protect your small business remote workforce

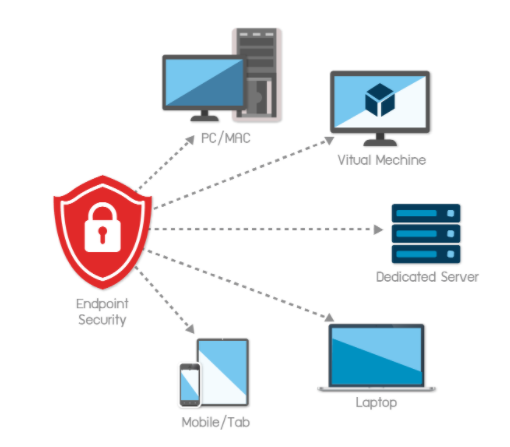
Sentinel One can be deployed on Windows, Mac and Linux servers, desktops, laptops, and workstations in seconds. With 24x7x365 Managed Endpoint Detection & Response service available, we bring you peace of mind and protect you from breaches that make headlines.
The first truly all in one cyber security solution for staff working from home due to COVID 19.
Purpose-built to protect the remote workforce
CyberHunter is pleased to offer the industry’s only cybersecurity solution that has been purpose-built to protect the remote workforce from advanced malicious attacks like ransomware, file-less exploits and zero-day attacks, Sentinel One.
View SentinelOne Video
Tomorrow’s Threats Require a New Enterprise Security Paradigm
REAL TIME - Endpoint Protection
Multiple patented AI algorithms protect against the widest array of threat vectors. Eliminate dependency on connectivity, cloud latency, and human intervention. On-device AI prevents known and unknown threats in real time.
ACTIVE - Detection & Response
Devices self defend and heal themselves by stopping processes, quarantining, remediating, and even rolling back events to surgically keep endpoints in a perpetually clean state. Hunt more and pivot less.
CLOUD DELIVERED | IoT Discovery & Control
SentinelOne Ranger transforms every device into a sentinel, mapping and enforcing the enterprise IoT footprint. Hunt rogue devices, ensure vulnerability hygiene, and segment devices with dynamic policies.
NATIVE | Cloud Security
Deploy autonomous CWPP across cloud, container, and server workloads. The building blocks of your secure cloud transformation are visibility, file integrity monitoring, protection, and compliance.
CyberHunter
Security Packages
PENETRATION INTO A BANK NETWORK USING TRANSPARENT NETWORK DEVICES
Legacy antivirus software is no longer sufficient to protect against these ever evolving threats. Whether you work from a personal desktop PC or a corporate MacBook, we have you covered with the world’s most advanced real-time endpoint protection solution.
We are so confident in the capabilities of this solution that it comes with a $1M ransomware warranty (contact CyberHunter for details). Sentinel One is a certified antivirus replacement.
Security packages for all shapes and sizes of business:
- 1 to 10 computers / servers
- 11 to 50 computers / servers
- 51 to 250 computers / servers
- 251 to 500 computers / servers
- 501+

CyberHunter
True Next Generation Endpoint Protection Features:
PENETRATION INTO A BANK NETWORK USING TRANSPARENT NETWORK DEVICES
- Static AI on the endpoint prevents attacks in real time.
- Highest efficacy and lowest false positives replaces any legacy antivirus.
- Behavioral AI detects malicious activities, no matter how they arrive.
- This is the only solution that can detect and prevent fileless, zero-day and even nation-state grade attacks.
- The Behavioral AI drives ActiveEDR to surgically remove and reverse any malicious activity in real-time. Never re-image a system again.
- World-class threat-hunting and forensic capabilities allow analysts to hunt more and pivot less.
- Eliminate human interaction and any dependency on cloud connectivity. Even the road warrior is protected.
- Ensure vulnerability hygiene across all devices
CyberHunter
Do Not Settle for Unnecessary Malware Dwell Time or Fake “Next Gen” Solutions
PENETRATION INTO A BANK NETWORK USING TRANSPARENT NETWORK DEVICES
Don’t be fooled by other solutions claiming to be “next generation”. There is a term that supposed “next gen” companies use when describing their detection and prevention capabilities. It’s called The “1-10-60 Rule” and it was coined by Crowdstrike because they need the rule to actually function. It means the following:
- They need 1 minute to detect an attack
- Then they need 10 more minutes to respond to the attack
- Finally, if they are lucky, they need only 60 minutes to remediate
Sentinel One doesn’t use that rule because it’s detection, response and remediation occurs in milliseconds. Not minutes, and certainly not hours. So if your protection solution needs the 1-10-60 crutch, you are using yesterday’s technology.
Free, No-Obligation Trial
Put us to the test with a no-obligation trial. Call us today.
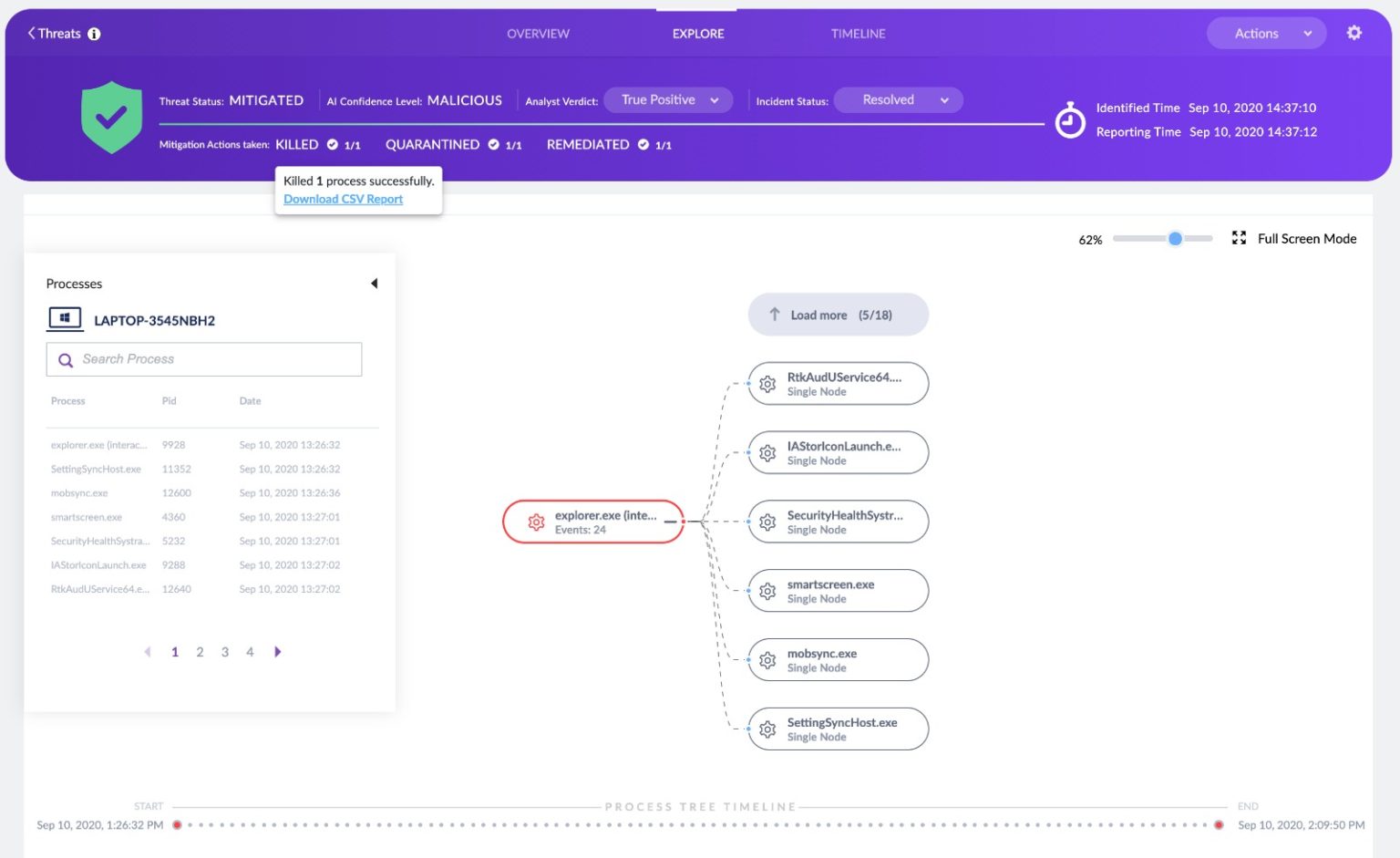
In today’s new reality, as we continue to work from home, we are missing the protection provided to us by the corporate network with it’s layers of defensive security controls.
BE PROACTIVE.
Trust in a network device is very temporary. Be proactive and ensure you scan, test and hunt on a regular basis.
TRUST NOTHING.
Security teams should NEVER trust an endpoint or server until it can be PROVEN to be trusted.
MALWARE CAN GET IN.
Companies need to prepare and be ready to respond to advanced persistent threats.

