There are a many reasons WHY organizations need threat hunting as a service, but the number one reason is that DEFENSE IN DEPTH DOES NOT WORK PERFECTLY. I know that we all love to talk about defense in depth as if that somehow, by adding enough defensive layers to the organization (i.e. the perimeter, the network, the hosts, the applications or even the data), every single attack will be stopped. I mean, the concept of defense in depth was created by the NSA, so it has to be good, right? How’s that been working out?
Of course, we NEED defense in depth. I am not saying we don’t. It is a best practice strategy for achieving information assurance, and it simply has to be done. However, the evidence is quite clear that malware and APTs will still get through your defenses…no matter who you are, and no matter how many layers you have protecting your network. Just when we think our collective lips are above the waterline, a new attack or exploit is identified and some poor organization is all over the news with a very public breach. I just love the phrase “next-generation” when people describe yet another cyber security silver bullet, because it implies that the previous generation didn’t do such a hot job….which of course it didn’t.
Anyhow, if you are an average enterprise in North America, then malware will typically sit inside your network for 6 to 8 months before someone (usually someone external) will find it. This is called the breach detection gap, and it can be narrowed if you acknowledge four simple guiding principles:
- Malware and APTs will breach your defenses.
- Never trust an endpoint unless you can prove it should be trusted.
- Established trust in an endpoint is a very temporary thing.
- Validate endpoints as malware-free, anytime, anyplace with Securitybox.
The Securitybox comes in three configurations (Alpha, Bravo, and Charlie) and can meet the scalability needs of any enterprise threat-hunting requirement:
Alpha: Focusing exclusively on the endpoints (Windows and Linux systems and servers) using agentless technology, this Securitybox configuration is for those who want to manually launch large-scale, on-demand (or scheduled) cyber threat hunts within their network.
Bravo: Designed for those enterprise customers looking for a zero-touch automated cyber threat hunting experience, the Bravo configuration of Securitybox adds an advanced packet analysis engine that monitors network traffic 24/7 looking for anomalous endpoint communication activity (e.g. beaconing, protocol tunneling, exfiltration, etc.). Upon detection of the suspicious network traffic activity, it will immediately launch an agentless endpoint cyber threat hunt that will analyze and validate the suspicion with no false positives.
Charlie: Designed for security analysts and cyber threat hunters who require a full-stack situational awareness of their network, Charlie configuration expands the Securitybox capability by adding access to a visually rich Cyber Intelligence Portal. The Charlie configuration allows analysts to easily explore and query their data, taking cyber threat hunting to the next level.
Practice good cyber hygiene with Securitybox.
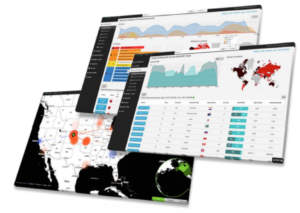
Securitybox-Charlie Screenshots

